Recognizing Potential Cyber Attacks Via Phishing Emails
If you turn on the evening news it is common to hear of the growing cybersecurity threats targeting sensitive healthcare information throughout our country. In 2019 alone, several studies have been released declaring that hospitals and healthcare offices are at an unusually high risk for such attacks. Perhaps you have read about the planned ransomware attacks targeting Los Angeles and San Diego health centers? Cyber attacks can be life-threatening in the case of high-level hospital centers; even for smaller local practices, the IT downtime and loss of EHR data can be devastating (not to mention the financial cost, which experts estimate can range into the millions of dollars). In light of these growing security threats, KSB Dental would like to take a moment to discuss what is perhaps the most commonly used scheme to infiltrate a healthcare provider’s practice… the phishing email.
A favorite trap of many attackers, the phishing email is one that on the surface looks to be innocent, but in reality, is anything but. In those cases, these messages appear to be from a legitimate source that you may actually do business with (e.g., Amazon, eBay, PayPal, major credit card companies). This appearance of credibility may, therefore, lead you to believe the message is authentic and that the request for information can be trusted.
In this tactic, the objective of the false email is to catch the recipient off guard by mimicking the format, layout, logo, etc. of a message from a legitimate source so that the victim, who may or may not do business with that entity, thinks this request is authentic. The attacker is sending these phishing emails out in large quantities, knowing that most individuals will not have an account with this company. However, they only need to fool a few recipients to make their scam profitable.
Once the victim has been misled into thinking that the email is authentic, they are now susceptible to following the email’s request which could ultimately lead to a cyber attacker gaining access to personal or sensitive data. However, if the recipient has been educated to look for some of the telltale signs that betray the dubious nature of this type of message, these scams are easily identified, and the crippling after-effects of such a nefarious request can be avoided.
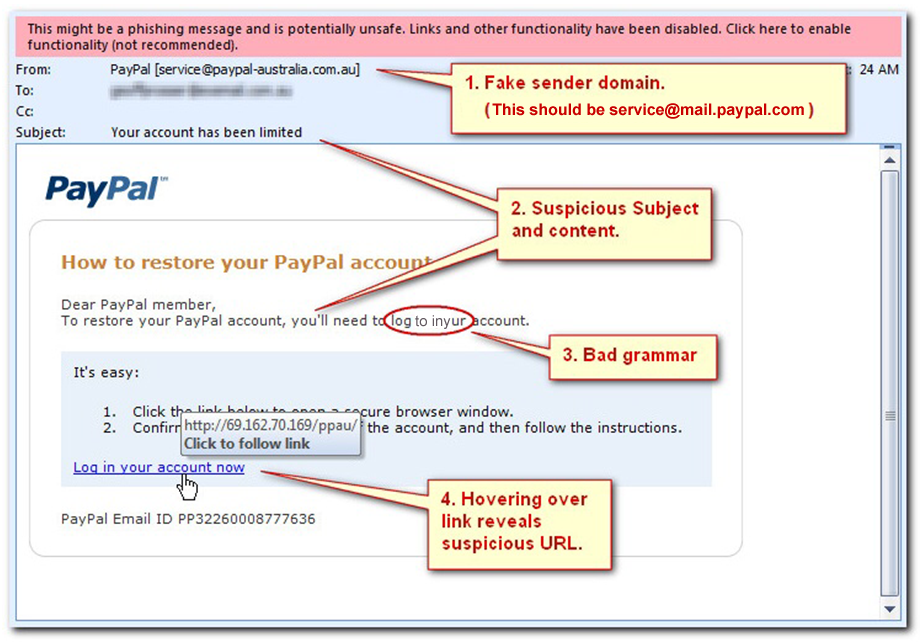
The image above is a sample of what a phishing email might look like… including the red flags that accompany it. You will notice that this email APPEARS to be from PayPal (complete with the official PayPal logo), and the overall layout seems to match the usual PayPal email format. However, the first tipoff that should arouse the recipient’s suspicion is the request itself. In reality, an email asking for information to “restore your PayPal account” should only be received if you have already initiated this process with PayPal. A request of this nature, appearing “out of the blue”, is one of the first red flags that the email may be fraudulent and not from the indicated sender.
Breaking the email down further, we can see that there are four additional red flags indicating this is a phishing scam. Figure #1 points to the sender’s email address. At first glance, it appears to be correct, but looking at the address more carefully, we can tell that it is not from “paypal.com”. The problem with the address is that it is a public domain email address. Most companies will not send emails from an address like @amazon.gmail.com or, in the case above, paypal-australia.com.au. (Amazon sends their emails from amazon.com, and PayPal uses mail.paypal.com.) This is similar to the way many of our customers have their own registered email addresses from their practice (e.g., drsmith@pediatrics4kidstooth.com instead of drsmithpediatrics4kidstooth@gmail.com). Incredible as it may sound, individuals with sinister intent will intentionally purchase similar domain names to make it look like their emails are coming from a legitimate source. If you wish to confirm the integrity of an email address used in a particular instance, just hover your mouse over the “From” field… the full address should now be viewable.
If you are ever concerned about the authenticity of an email, you can always log in to your account through the actual website address (e.g., go directly through Paypal.com) or reply to the sender to see if they recently emailed you. Sometimes email systems can be hacked and used to generate “masked” cyber attacks, without the owner even being aware of it!
Figures #2 and #3 identify other suspicious characteristics of this type of email. It is common for the subject line and/or the body of the email to be vague, and these schemes often use both misspelled words and bad grammar. In this example, note that the email does not mention why the account has been limited. A legitimate warning from Google, Apple, Amazon, etc. will provide details of any alert, such as “an attempted login from Mumbai, India was blocked”.
Figure #4 points to the actual scam link directing the victim to “log in to your account”. By hovering your mouse over it, a small display will then pop up, showing where the link takes you. Here, we see the link is an IP address (four numbers separated by dots). Sometimes it will direct recipients to a “mimicked” website which will then compromise your computer. This malware can also come as an email attachment, such as a pdf file. It is common for such files to be labeled as “Invoice.pdf”. Again, most of these infected files come with the malicious software already installed, waiting to spread from your computer all the way up to the practice servers. These attacks can range from ransomware (software that essentially encrypts all of your sensitive data and holds it hostage until the victim pays a large sum to the attacker) to stealing and sharing your sensitive ePHI (electronic protected health information) and financial information (saved credit cards, etc.).
While anti-virus software can be effective in aborting ransomware and malicious attacks, the threat may come in a form that has yet to be recognized by the protective software. According to Verizon’s 2019 data breach investigation report, 32% of ALL cyber attacks involve phishing emails. By learning to recognize the red flags that are associated with these attempts, you and your staff can greatly reduce the risk of practice downtime and the financial burden that often comes with successful attacks. KSB also strongly suggests that your office maintains a regular backup of its data, and has detailed the importance of backups in our January 2019 issue. Additionally, you can read about our “Five Easy Steps” to securing your patient data in our August 2018 newsletter. If you have any questions regarding phishing emails, or if you believe your office may have been compromised, please contact Danny at KSB support.